Solution Components
A deployment of the AccessAnywhere Enhanced Security Architecture involves
four components deployed across three tiers. Each of these tiers may
consist of one or more systems/servers.
The three tiers are as follows:
- Internet device
- Demilitarized Zone
- Production Network
The four components are as follows:
- Client
- AccessAnywhere Gateway
- AccessAnywhere Server
- Corporate Applications
|
AccessAnywhere Baseline Deployment
In its base deployment AccessAnywhere consists of just one
system that is typically deployed into the DMZ environment. This system then
connects directly to servers on the Production Network through a back-end
firewall. In order to simplify firewall configuration and enhance security,
Caveo offers an Enhanced Security Architecture Option, which allows for
all data and direct communications with the Production Network to be handled
by an AccessAnywhere Server on inside of the Production Network. An AccessAnywhere
Gateway remains in the DMZ to act as a communications proxy providing perimeter
security services.
The remainder of this document discusses each of the four components (Client, AccessAnywhere
Gateway, AccessAnywhere Server,
and Production Systems) associated
with an Enhanced Security deployment.
AccessAnywhere Enhanced Security
Architecture Deployment
Client
The client is any device (i.e.. PC, Mac, Unix, PDA, etc.)
that is connected to the internet (i.e. Dial-up, ISDN, Cable, ADSL, T1,
etc.), and is running a Java (JDK 1.1) enabled internet browser (i.e. Internet
Explorer, Netscape Communicator). All communications initiated by the client
is performed using an Secure Sockets Layer (SSL) secured
connection.
AccessAnywhere Gateway
The AccessAnywhere Gateway is a Sun/Solaris system with
has been implemented with the Solaris Security Toolkit which provides a
flexible mechanism to minimize, harden, and secure the Solaris Operating
Environment. All non-essential services are disabled and external access
is only available through Secure Shell (ssh). The Gateway is traditionally
deployed in the DMZ (Demilitarized Zone) and is the only server that remote
clients actually communicate with. The Gateway supports client SSL connections
using the same SSL V3 ciphers as the browsers. Server certificates can be
either self-issued, or generated by any number of public Certificate Authorities.
Although the Gateway enforces access rules, there is no data stored on the
Gateway, and there is no need for the Gateway to communicate to any other
system in the Production Network other than the AccessAnywhere Server. Communication
with the AccessAnywhere Server can take place using either HTTP (default)
or HTTPS, depending on an organizations security requirements.
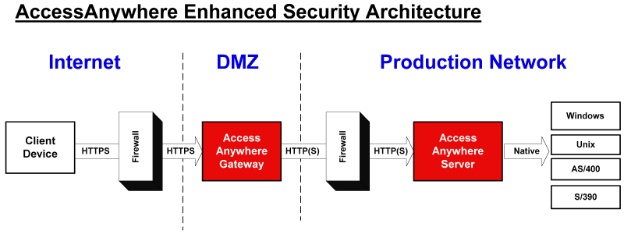
AccessAnywhere Server
The AccessAnywhere Server is also a Sun/Solaris system
with has been implemented with the Solaris Security Toolkit, to ensure the
highest levels of security. The AccessAnywhere Server is traditionally deployed
on the Production Network and acts as the delivery control point for all
corporate applications and data. The AccessAnywhere Server accepts HTTP
(HTTPS can be enabled) connections from the AccessAnywhere Gateway,
and initiates connections with servers on the Production Network using their
native protocols. Security of the native protocols are defined by the various
protocols being used and the network and system security in place on the
Production Network.
The AccessAnywhere Server maintains all of the rules and profiles associated
with AccessAnywhere users and initiates authentication requests to sources
on the Production Network for authenticating users. Authentication, Authorization,
and Encryption are the three important elements
as they relate to security of an AccessAnywhere solution. Each of
these are discussed in detail below.
Authentication
AccessAnywhere can support a number of authentication
methods. Although basic username and password authentication is possible
via LDAP, Radius, NT Domain, etc, it is highly recommended to use a two
factor authentication method, such as digital certificates (X.509V3) or
hardware tokens.  The preferred method of authentication is RSA SecurID tokens, due to
the mobility and platform independence that they provide. Each RSA SecurID
displays a unique code generated by the patented RSA SecurID hash algorithm
in combination with the unique 64-bit symmetric key contained in the token.
Augmented by an internal clock, the algorithm generates a new code every
60 seconds for the programmed life of the token. The number displayed at
any given point in time is unique to each SecurID token, and is known only
to the corresponding RSA ACE Server. This hardware token is a standard-sized
fob that connects easily to any key ring and fits into a user's pocket or
small carrying case. To authenticate using the RSA Securid token a
user provides their username and a passcode which is a combination of a Personal
Identification Number (PIN) and the tokencode that is shown on the token
at the time. To compromise this two-factor authentication, a potential hacker
would have to both know the users PIN, and be in possession of his/her token.
When RSA SecurID is included as part of an AccessAnywhere deployment, it
is typically placed as part of the AccessAnywhere Server. If an existing
RSA ACE Server already exists in an organization the AccessAnywhere Server
can act as a client to that existing server.
The preferred method of authentication is RSA SecurID tokens, due to
the mobility and platform independence that they provide. Each RSA SecurID
displays a unique code generated by the patented RSA SecurID hash algorithm
in combination with the unique 64-bit symmetric key contained in the token.
Augmented by an internal clock, the algorithm generates a new code every
60 seconds for the programmed life of the token. The number displayed at
any given point in time is unique to each SecurID token, and is known only
to the corresponding RSA ACE Server. This hardware token is a standard-sized
fob that connects easily to any key ring and fits into a user's pocket or
small carrying case. To authenticate using the RSA Securid token a
user provides their username and a passcode which is a combination of a Personal
Identification Number (PIN) and the tokencode that is shown on the token
at the time. To compromise this two-factor authentication, a potential hacker
would have to both know the users PIN, and be in possession of his/her token.
When RSA SecurID is included as part of an AccessAnywhere deployment, it
is typically placed as part of the AccessAnywhere Server. If an existing
RSA ACE Server already exists in an organization the AccessAnywhere Server
can act as a client to that existing server.
Authorization
Within the scope of the entire system, authorization
is addressed at three levels:
- Access day and times are determined by the RSA ACE Server upon
initial authentication.
- Applications and data that are going to be made accessible to
the user is controlled by the AccessAnywhere Server and enforced by the
AccessAnywhere Gateway. The Gateway configures the AnywhereClient applet
with security rules based on each users personal profile. This security
profile determines on what local ports the AnywhereClient will accept connections,
and to what corresponding production server:port pair the connection should
be mapped. Administrators may configure users to inherit authorization
rules from their specified role, or customize on a user by user basis.
- Explicit application authorization is determined by the specific
authorization metrics of each application for which access has been granted.
Encryption
There are three different usage scenarios within AccessAnywhere:
AnywhereWeb(HTML Web content), AnywhereClient (Thick Client local execution),
and AnywhereApplication (Thin Client remote execution). Each are discussed
below.
AnywhereWeb
AnywhereWeb deployments provide access to Intranet applications running
on Web Servers on the Production Network. Once a user has authenticated
and connected to the AccessAnywhere Gateway, they are presented with either
an AccessAnywhere Webtop or an internal portal/web site. From here they
can access any Intranet content for which they have authorization. Connections
from the client to the AccessAnywhere Gateway are all encrypted using SSL regardless of whether the internal Intranet sites are
using SSL or not.
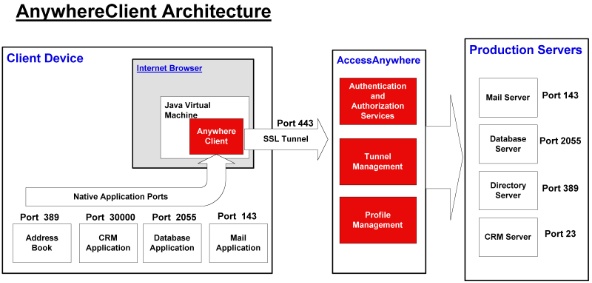
AnywhereClient
AnywhereClient deployments are typified by local client applications executing
on the client device that require connections to servers on the Production
Network. To instantiate a connection to the corporate servers a user launches
their local internet browser and connects to URL mapped to the AccessAnywhere
Gateway (i.e. https://accessanywhere.caveo.ca). As indicated in the example,
the browser is connected to the Gateway via a secure SSL session. When
this session is first established, the AnywhereClient, which is a small
proxy applet is downloaded and run within a small browser window. AnywhereClient
establishes an SSL tunnel with the AccessAnywere Gateway. Once established
any local TCP/IP enabled application can utilize the SSL tunnel to connect
to servers on the Production Network. To do so, local client applications
(ie Microsoft Outlook) initiate a connection to the remote destination server,
using their standard port(s). This connection is 'redirected' through the
AnywhereClient tunnel to the AccessAnywhere Gateway. Provided the users session
is still active and they are permitted to connect to the services requested,
the request is passed on to the AccessAnywhere Server, where it is taken out
of the HTTP(S) tunnel and placed back onto the production network as the
native protocol, before reaching the destination server. Note that the AnywhereClient
will only accept requests on its localhost (127.0.0.1) address, and therefore
there is no risk of outside systems gaining access to production servers
through the SSL tunnel.
The following sample AnywhereClient ruleset highlights the ennablement
SMTP, IMAP, HTTP, and Telnet access to the four discrete servers named smtp,
imap4, www, and unix, respectively. Dynamic rules can be enabled for dozens
of servers and ports.
Netlet rule 0: local:25 destination:smtp.caveo.ca:25
Netlet rule 1: local:143 destination:imap4.caveo.ca:143
Netlet rule 3: local:8000 destination:www.caveo.ca:80
Netlet rule 4: local:30000 destination:unix.caveo.ca:23
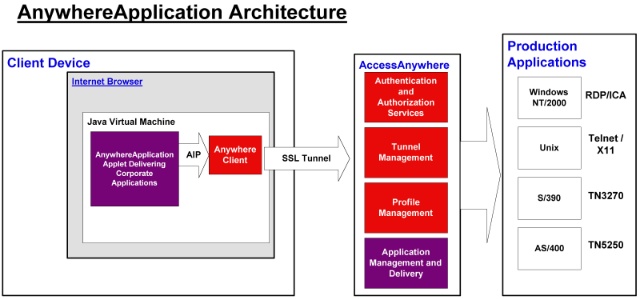
AnywhereApplication
In AnywhereApplication deployments, clients still have
all of the capability of the AnywhereClient SSL tunnel, however, client
applications are actually executed on servers on the Production Network.
These applications are all accessed through a Java enabled internet browser,
hence the thin client. All communications with the corporate applications
takes place via Java applets that are dynamically downloaded. These applets
utilize the AnywhereClient tunnel functions to secure their communication
requirements to production servers.
SSL
As noted above the AccessAnywhere solutions leverages industry standard
SSL technology for encryption. AccessAnywhere supports the same strong encryption
available in current internet browsers. The following strong SSL V3 ciphers
are supported for key exchange, encryption and digital signatures:
- RC4 encryption with a 128-bit key and an MD5 MAC
- FIPS 140-1 compliant triple DES encryption and SHA-1 MAC
- Triple DES encryption with a 168-bit key and a SHA-1 MAC
- FIPS 140-1 compliant DES encryption and SHA-1 MAC
For more information on SSL see http://docs.iplanet.com/docs/manuals/security/sslin/index.html
Production
Systems
AccessAnywhere is a non-intrusive system that does not
require any changes to existing networks, servers or applications. AccessAnywhere
interacts with these production systems in their native format, and simply
allows access to be extended beyond the corporate LAN.
|



